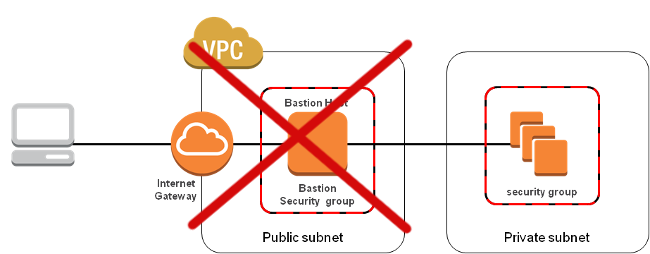
Ec2 instances can be secured with security groups this is a basic firewall that allows you to open and block network access to your ec2 server.
Aws network acl vs security group best practices.
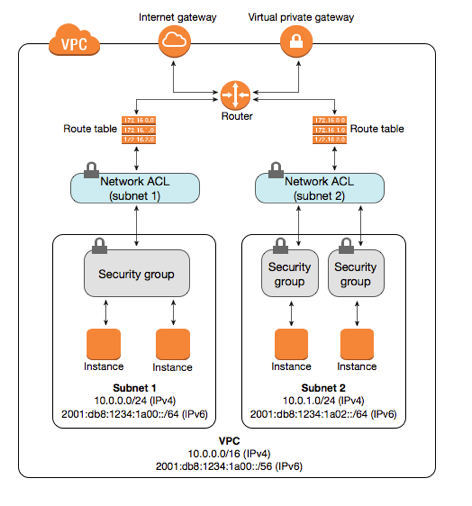
Aws network acl rules both inbound and outbound are defined in terms of the destination port the numbering can start at one and go as high as 32766.
For more information see security groups for your vpc and network acls.
A security group acts as a firewall for our ec2 instances.
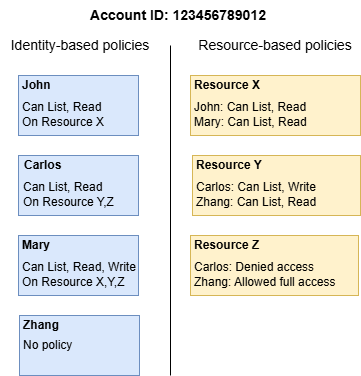
Use iam policies to control access.
Welcome to part 11 of a multiple part course on passing your aws architect developer sysops associate exams.
While assigning it is recommended to leave a gap of at least 50 numbers between each of the nacl rules so that there s enough room for additional rules in the sequence for use later.
Close unnecessary system ports.
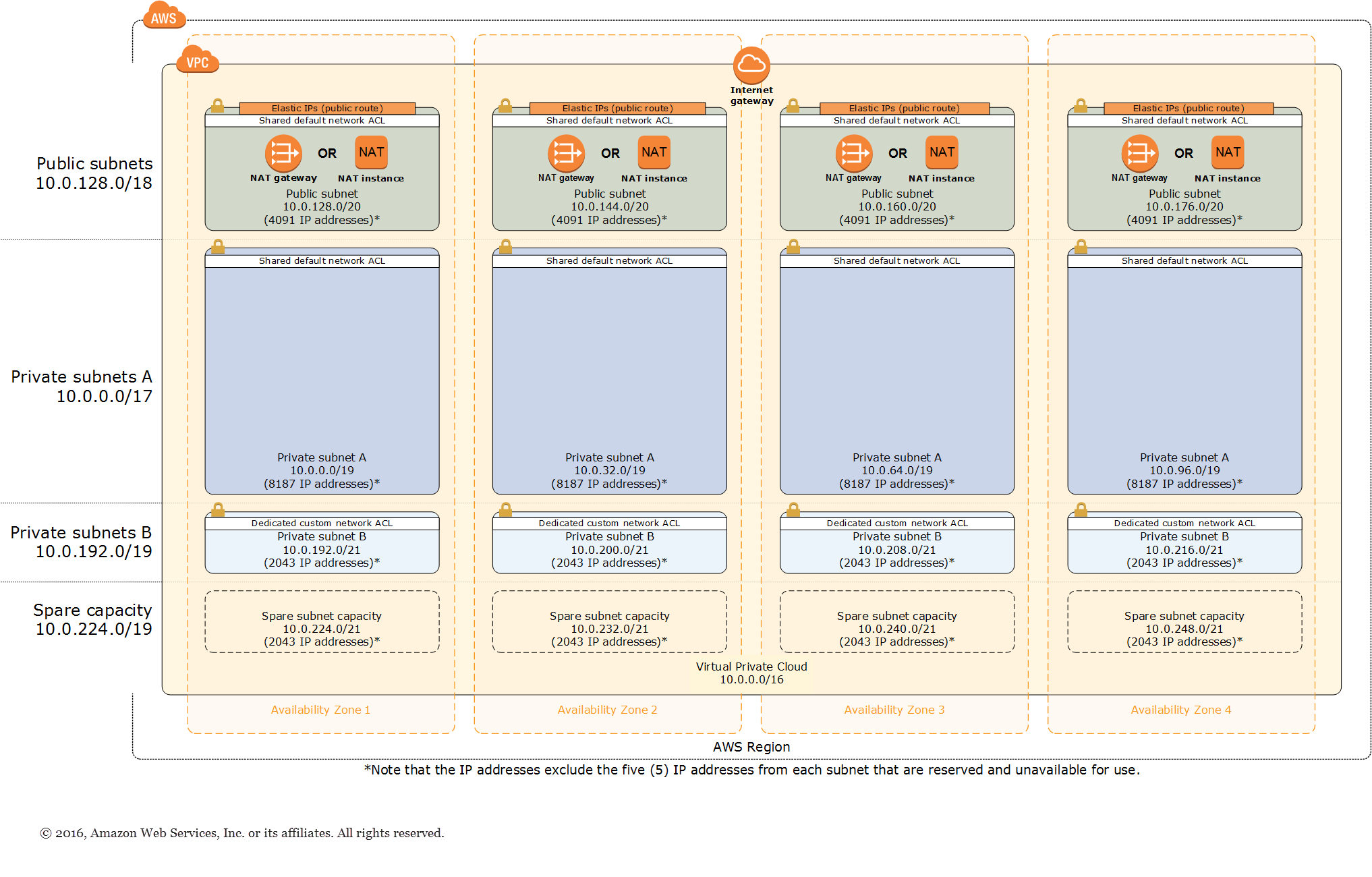
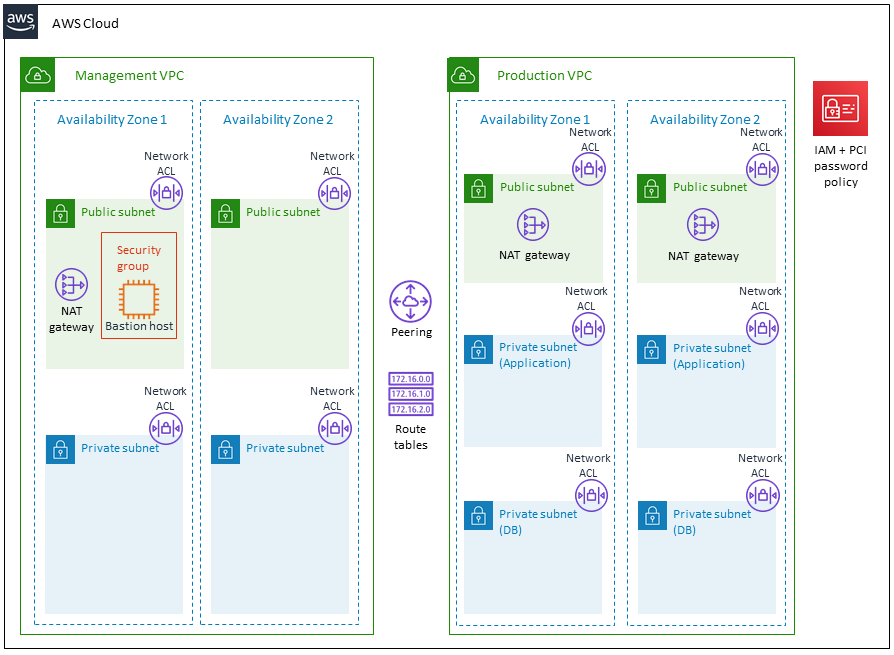
You might set up network acls with rules similar to your security groups in order to add an additional layer of security to your vpc.
Security groups evaluate all the rules.
The best part this course is totally free of charge.
The below illustration shows a high level view of the security group.
Aws network acl.
In one of our previous posts we spoke about 5 not to ignore best practices for aws security groups.
This post looks at the best practices for aws security groups and how these practices can help protect your data by restricting access to certain ip addresses.
A network access control list acl is an optional layer of security for your vpc that acts as a firewall for controlling traffic in and out of one or more subnets.
In this post we will walk you through a few best practices for nacls.
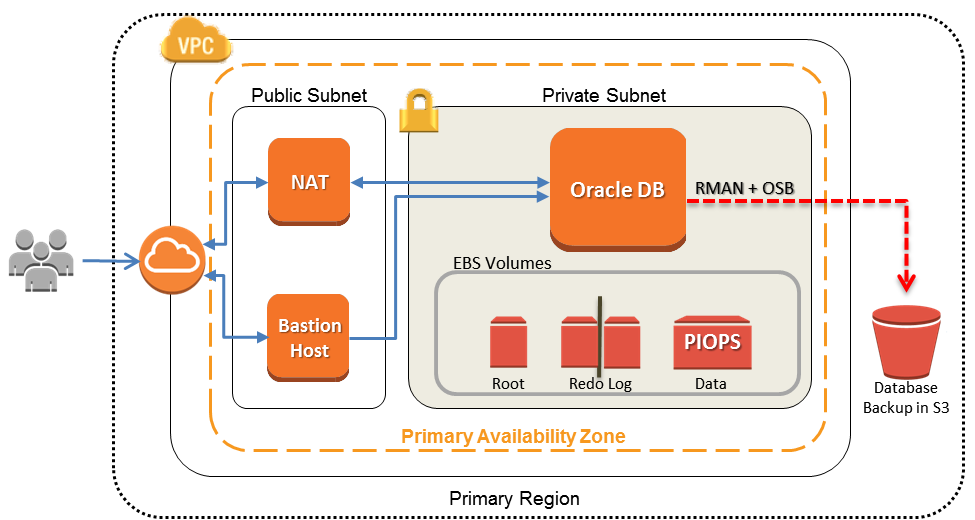
This document details best practices to configure security groups in aws for clustrixdb.
All rules in a security group are applied whereas rules are applied in their order the rule with the lower number gets processed first in network acl.
Harish ganesan 27 best practice tips on amazon web services security groups cloud big data and mobile.
Use flow logs to capture information about ip traffic going to and from network interfaces in your vpc.
Security groups are the fundamental base of network security in aws.
Using the default security group firewall settings provided by amazon can get customers up and running quickly but these settings do not provide the best database network security.
In other words security groups control how traffic is allowed into or out of our ec2 instances.
Use security groups and network acls.
In this article we ll compare and contrast network access control lists nacl and security groups and explain when you might want to choose one over the other.